Understanding Multi Factor Authentication – The Pros and Cons
Password security is the foundation for keeping your information and data safe but with cybercrime on the rise, the likelihood that bad actors also know your password is high. Indeed 81% of hacking related breaches are caused by weak or stolen passwords.
Multi factor authentication (MFA) is a commonly used identification tool used to provide an additional layer of authentication (factor) and stop accounts being compromised. In fact, MFA can block over 99.9 percent of account compromise attacks. While a cybercriminal may have your credentials, adding a mandatory additional factor provides additional proof that you are who you say you are.
Many services are implementing passwordless security strategies but when you need to add a second factor of authentication to an account that is already protected with a password, it’s essential to know the pros and cons of each type of MFA. In this blog we examine the different categories of multi authentication factors, review how commonly used types of MFA work and consider which is the strongest.
Types of Authentication Factors
Typically, authentication factors fall into three main categories:
Something you know
Something you have
Something you are
The most common authentication factor used is a password, and this falls squarely in the ‘something you know’ category. Other types of this information could be the PIN to your credit card, or a door access code for example.
The ‘something you have’ category is quite broad and the way this is technically implemented varies greatly. For example, ownership of your phone number proved via an SMS code, or ownership of a physical FIDO2 paswordless security key.
The final category of ‘something you are’ typical relates to biometrics. For example, using your face ID to unlock your iPhone, or a fingerprint to unlock your banking app.
Understanding Common MFAs
There are many different types of factors available in each of these categories and understanding how these work can ensure you can manage the risks to your data.
Security questions
One of the oldest styles of MFA, falling squarely in the ‘something you know’ category, security questions are often seen in the banking industry and rely on personal details that are unlikely to be commonly shared. For example, what was the name of your first pet or your first school? While potentially easy to remember, if your life is of public interest the information may be known widely creating a significant weakness.
Email token
Typically, this type of MFA involves receiving a six-digit code via email, so would be ‘something you have’. This code is then used to complete the sign in form after your username and password. This method is fairly secure but relies on the security of your email account. If an adversary is able to compromise your email account, or your email is not protected by MFA, they will also have access to these codes.
SMS token
Similar to the email token outlined above, and again ‘something you have’, an SMS factor is typically a six-digit code sent to your phone. The benefit this has over the email token is that you need access to your phone number to receive the SMS. However, if your phone is compromised and a cybercriminal has gained an account password from this, then they will also have access to the SMS codes. Compromising a mobile phone is a more complicated than brute forcing a username and password combination for an online service, but for high value individuals, cyber criminals may use this approach alongside SIM swap attacks.
Time Based One Time Password (TOTP)
Using a TOTP requires the installation of a specific app such as Microsoft Authenticator, Google Authenticator or Duo Mobile. Once in the app you would typically scan a QR code to display the six-digit code (something you have) required for access to the service. This code will refresh at fixed intervals, typically every 30 seconds, although it can be valid for any length of time. In addition, the code can be used before or after the current one, so the current, previous or next code in the cycle remain valid for each interval.
This type of MFA is very secure as it requires access to the device the TOTP app is installed on. Ideally a separate device would be used to handle TOTP generation otherwise there is still a risk of your phone being compromised and the adversary being able to access the service. In this case back up codes must be stored carefully.
Passkeys
Passkeys are a relatively new method of MFA and make use of a standard called FIDO2. This is the latest specification issued by the FIDO Alliance, an open industry association with a mission to reduce the world’s reliance on passwords. When you add a passkey to an account your device will generate a pair of keys (something you have) and share the public part with the service you are authenticating to. Then when the service wants to validate that you are who you say you are, they will issue a request to you which will be digitally signed using your private key.
The user experience with this method is excellent, it takes minimal time and provides a very high level of security. The key downside is the risk of losing your device which would restrict access to your account. To mitigate this risk, we recommend adding passkeys from multiple of your devices.
Hardware Tokens
Hardware tokens are another type of FIDO compliant MFA solutions. They work in the same way as passkeys but instead of the key pair being generated on your phone or laptop, they are generated on an external device that is usually a USB stick (something you have). The keys can’t be removed from the device which makes these even harder to compromise. When you try to log in to a service with a hardware token you will usually have to tap the token physically to complete the challenge-response. This provides another level of security as someone who has compromised your laptop will not necessarily be able to physically touch the hardware token.
Magic Links
A magic link is similar to an email token with the exception that no initial password is required. Entering your email address will generate a special link (something you have) which when clicked, will automatically log you in. This is handled entirely by the service you are trying to log into, and you don’t need to do anything to set this up making this an easy method of MFA to use. However, as the magic link can sign you in, it's important that this is protected. Unfortunately, some emails still traverse the internet unencrypted which means your magic link may be exposed.
Push Notifications
Using custom apps that are installed on your device, some providers push a custom notification to you each time you try to log in. The notification will prompt you to confirm your action, either by simply hitting an ‘ok’ button or requiring you to enter something they have displayed on your other screen. In both instances, this factor confirms you have access to your Push Notification app at the same time as your log in attempt.
While this is an easy to use ‘something you have’ option, removing the need for a password in some cases, very few services support this method. A key downside here is losing your device could mean you are locked out of your account.
Biometrics
There are many types of biometric authentication (something you are) but the most commonly used are facial recognition and fingerprint. To make use of these types of MFA you need to have a device with the capability. Typically, this is a mobile phone, but most laptops now have fingerprint readers and cameras that are capable of scanning a face.
When you configure your face or finger on your device a representation of your biometric information is stored in the secure enclave of your device. You can then allow a service to make use of this protection by adding your biometrics as a second factor. This often makes use of the WebAuthN standard which will generate a public/private keypair and share the public part with the service. It will then store your private key and protect it with your biometrics.
When you authenticate your biometrics unlock the private key and this is then used to sign a challenge issued by the service. This is a strong protection measure, but it can hinder usability as it requires access to your device. If you lose your device, you also lose the ability to prove your own biometric features.
What is the strongest type of MFA?
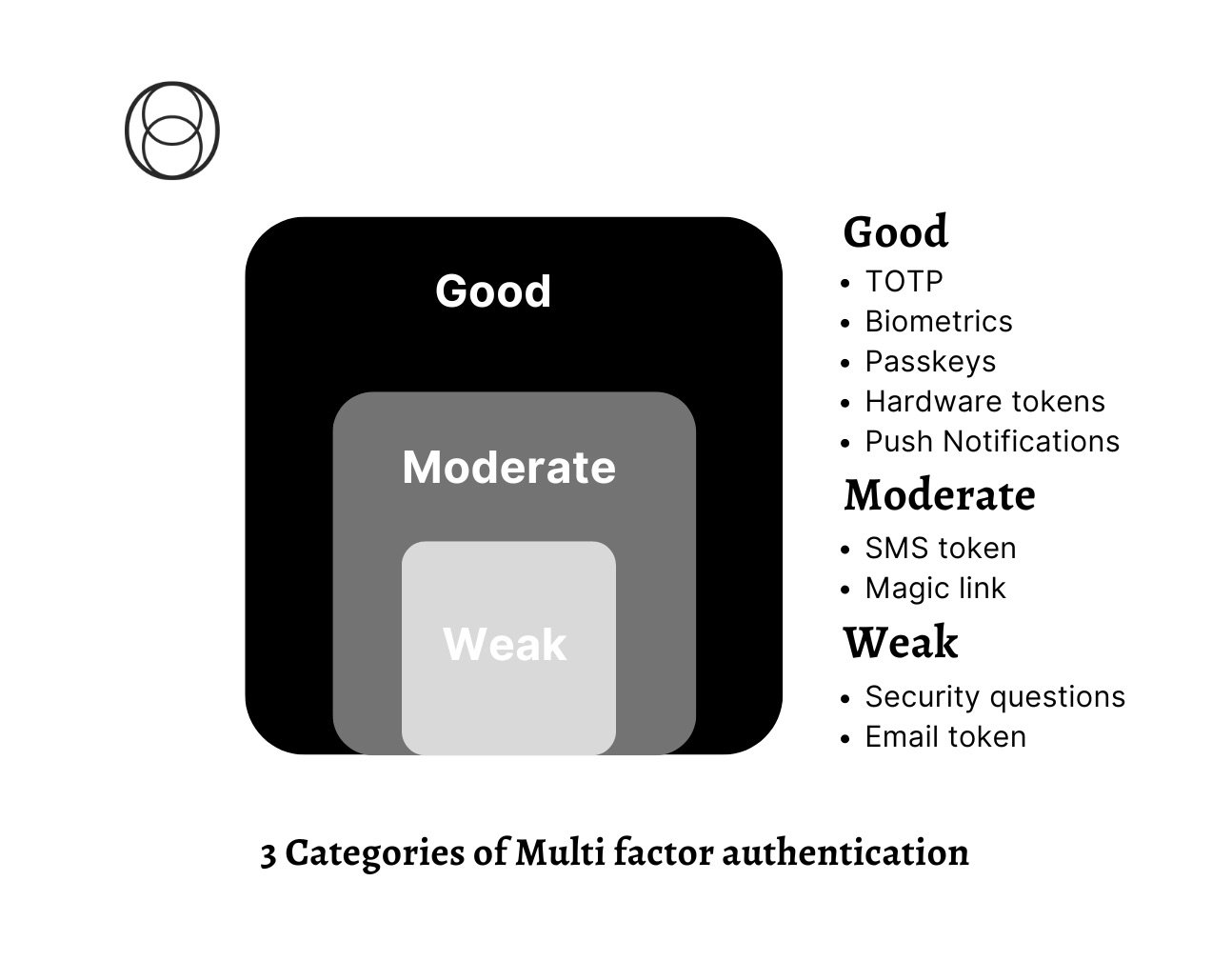
As cybersecurity experts, we regularly get asked what type of MFA is the strongest. While it’s not completely straightforward, we generally group them into 3 categories: weak, moderate and good.
The strongest means of authentication is a combination of the three types listed above. Ideally those in the good category. It is important to note that when using MFA, you should not use two of the same factors. It would not provide much more security by having two passwords, but it does add a lot of security if you have a password and a hardware token.
For anyone still unsure, using any form of MFA is far better than none, and it's crucial to implement the most secure options on your most sensitive accounts, such as your email and bank accounts.
Want to learn more about mobile device security? Get in touch with coc00n today.
Cybersecurity Awareness Month is an international initiative that educates everyone about online safety and empowers individuals and businesses to protect their data from cybercrime.